The digitization of business processes and the performance of IT systems are increasingly critical for companies to remain competitive and prepared for the future. To ensure smooth IT operations and minimize risks, companies need a well thought-out plan – ideally in the form of IT risk management. But what measures should the strategic plan include and what current IT risks need to be taken into account? Hanno Schaz, Head of Security Operation Center and Incident Response at DGC, addresses these questions in our interview:
As the opportunities of digital transformation increase for companies, so do the risks: In its latest security report, the German Federal Office for Information Security (BSI) has declared a red alert for some areas. Which organizations need strategic IT risk management nowadays?
From global corporations to medium-sized businesses to one-man operations, companies of all sizes should pursue the idea of IT risk management. The effort and scope of risk management are related to the individual requirements and framework conditions of a company.
What exactly does the term IT risk management mean and to what extent does it help to meet the challenges in the age of digitalization?
Awareness and transparency of IT risks provide the foundation on which information security management or business continuity management can be built. The first step is to identify the information assets – i.e., the document that is used on a daily basis, the company’s own notebook, the file share, or the application that is urgently needed for work – and the associated risks for operations before they can be secured. Another important step on the path to more security is risk assessment – IT experts refer to this as criticality.
Overall, the aim is to achieve comprehensive transparency about the current technological status of the company in order to be able to counteract risks as quickly and effectively as possible. For some decision-makers, the initial outlay and ongoing maintenance will initially seem cost-intensive. However, these costs are out of all proportion to the economic damage if the entire operation comes to a standstill in the event of an emergency.
Risk management decisions should comply with the maxim of cost-efficient risk management: It is therefore necessary to weigh up on the basis of facts and figures: What (financial) consequences could possible impact scenarios have, how likely is their occurrence, and what do effective countermeasures cost?
What measures should effective IT risk management generally include?
Risk management consists of a series of measures such as defining a strategy and role responsibilities. It should also be defined what exactly constitutes an incident, emergency, crisis or even disaster for the company and what real dangers exist. By developing strategies and plans for dealing with emergencies – such as an emergency concept for the failure of Active Directory, one of the central components for managing Windows-based networks – responsible parties become able to act. And they do so precisely when it matters and when the very existence of the company may be at stake.
Ideally, emergency management establishes measures to be able to switch to emergency operation at very short notice, for example, and thus maintain the company’s productivity. In contrast, without a clear emergency strategy, it usually takes a long time for a coordinated team to restart the systems. Time that can quickly lead to immense costs and should therefore be kept to a minimum.
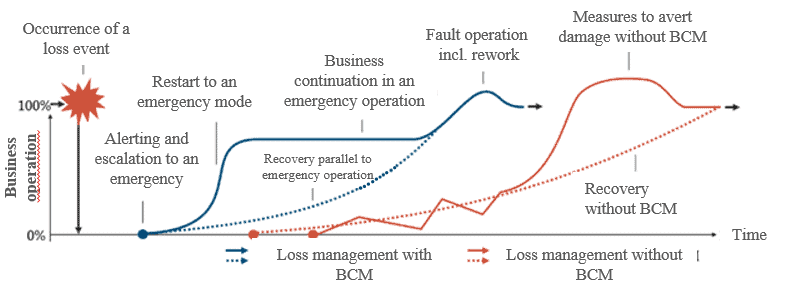
Business continuity management (BCM) ensures that business activities are maintained in the event of an incident with a crisis-proof IT concept. Well thought-out IT risk management forms the basis for this.
Let’s take a look at the practical side of things – what are the typical IT risks for companies in 2022 that they need to protect themselves against?
One of the greatest dangers is posed by humans themselves: Most errors happen due to faulty operation of systems, negligence or deliberate harmful actions. This can be countered through training and emergency exercises, so that all employees move from being a risk to being a protective measure. With the appropriate training, they can actively contribute to preventing hacker attacks by, for example, reporting anomalies in systems or phishing attempts to IT, thus preventing the installation of malware (ransomware) and the unintentional leakage of sensitive data.
The life cycle of existing IT systems also often proves to be a difficult issue for companies. Security managers should regularly ask themselves: How long can we continue to operate which IT components? How do we deal with systems that may be designed to run for ten, twenty or thirty years? The associated risk is primarily that of patch availability, since systems must be repeatedly supplied with security patches (updates). If this is no longer possible, security gaps and vulnerabilities arise – and with them new gateways for cybercriminals. In addition, not every IT system can simply be switched off after the official end of maintenance. This is where forward planning pays off in order to avoid dangers and costs.
Another risk is the issue of incorrect configuration of systems. Configuration management can help to deal with this problem by means of a configuration management database (CMDB). However, a CMDB cannot be operated without appropriate change management, which brings us to the fourth risk – that changes to IT systems are not traceable or associated risks are not assessed. To ensure the effectiveness of change management, IT risk management should be integrated into the decision-making processes for releasing changes.
Are there other current cyber risks that managers should consider in their IT risk management? For example, with regard to the increasing relevance of digital platforms and global cyber ecosystems?
Indeed, attacks on upstream service providers represent another very real security risk. Maintaining information security along the entire value chain of companies and their partners therefore plays an increasingly important role. Often, supplier management is still inadequate in this regard. DGC starts at this point and supports companies in establishing high security standards within the entire cyber ecosystem. This requires expertise as well as powerful IT security tools that enable permanent monitoring and defense of the systems.
Who should be responsible for IT risk management in companies? What competencies does this person or group of people need?
Risk management places relatively broad demands on a person or group of people who are responsible for identifying and assessing risks, operating them, and further developing the plans and strategies for managing them. In order to obtain a holistic overview of the risks, human factors, technical and also process aspects of IT operations as well as the entire organization must be considered.
It is not only IT administration that plays an important role when it comes to technical aspects. It is also about issues far removed from IT, such as protection against natural hazards if, for example, there is a water ingress. In addition, all aspects of power supply should be considered – for example, the use of systems for uninterruptible power supply.
The main person in charge should accordingly be broadly positioned in order to understand the diversity of topics. At the same time, sufficient commercial skills are needed to operate a cost-efficient risk management system. A good overview of existing standards or best practices completes the competence portfolio so that established standards are applied when developing strategies.
In addition, those in charge should know that they are not on their own when it comes to a complex task such as the introduction of IT risk management. Specialized service providers such as DGC provide support with know-how and IT solutions – and thus ensure an efficient and cost-sensitive approach.
In the second part of the expert interview, you will find out how strategic risk management can be established in IT, which risk analyses are helpful in this process, and what role cyber insurance plays in this context.




